Don’t Fear the Cloud (or Kubernetes): Your Google Security Questions Answered
During Activate, Mike Chesnut, our Senior Director of Cloud Ops chatted with Tiffany Lewis, Google Cloud’s Security and Compliance Specialist. Chesnut and Lewis shared information about Google’s Kubernetes solution and why working with the Google Cloud Platform offers one of the most secure, scalable cloud services in the market.

GCP and Fusion: A Perfect Match
Lucidworks partners with Google’s Cloud Platform (GCP), because they provide us and our customers with the best possible experience. We run Fusion 5 on GCP and use Google’s Kubernetes Engine (GKE) to help us containerize our data at scale. GCP lets us take advantage of their undifferentiated heavy lifting – they do the work of managing the cloud network so we can focus on what our customers need us to do – power their advanced search and data discovery.
GKE is the most advanced Kubernetes offering – they auto-scale, auto-upgrade and auto-repair and do all of the integrated monitoring. They are, of course, secure by default. Security is table stakes for any cloud provider and Google takes it as seriously as any provider can. There’s physical security in their facilities but the data is encrypted and secured by multiple layers of compliance discipline.
The GKE helps us isolate our workloads and we get to build on the strong foundation of security that GCP provides us – we can leverage that foundation by building on the shoulders of giants to meet every requirement. It’s like having an in-house Kubernetes team without having to employ them and our software runs more smoothly.
FAQ on GCP Deployment
At Activate, Lewis talked the audience through the process of deploying GCP, step-by-step, including what’s given to customers out of the box, what they inherit by working with GKE and some of the shared responsibility necessary when working in a public cloud infrastructure.
Of course, the legal disclaimer needs to come first: Google Cloud is an enterprise business. It needs to be said that GCP runs completely differently than the consumer side of the house and the ads business. Your data is your data, not Google’s. They employ several layers of security to ensure Googlers never see customer data – in fact, all of the data is encrypted both in transit and at rest. They have technical and contractual controls against actions and they liaise with independent, international third parties – no government entity can receive any “backdoor” access.
With that out of the way, Lewis goes on to explain that Google encrypts at rest by default – one of their major differentiators. There’s nothing that customers have to do to activate the encryption. A secure foundation is the best way to start any cloud journey.
Now let’s talk about the data workflow journey. We’ll keep this fun and use the example of what happens when a cute video of a frolicking puppy enters the Google Cloud as a piece of data.
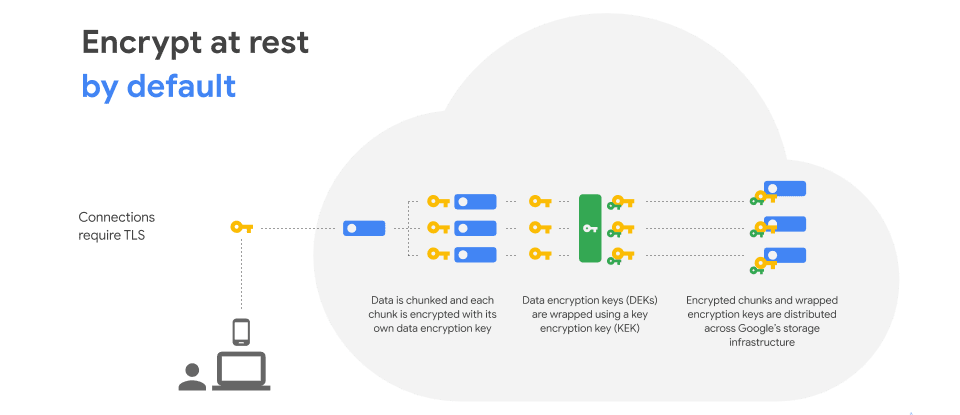
All of the pieces, at the start of the data flow journey, are a mish mash. The pieces of the data could be coming from all sorts of locations – the puppy video could enter the data workflow from anywhere on the web, or within a customer’s data flow. Eventually, however, through the GCP encryption process, the data points are all organized and ultimately land in a secure storage infrastructure. You can see above that there are several layers of encryption throughout this process.
Let’s talk about the multitude of high-level security differentiators at GCP:
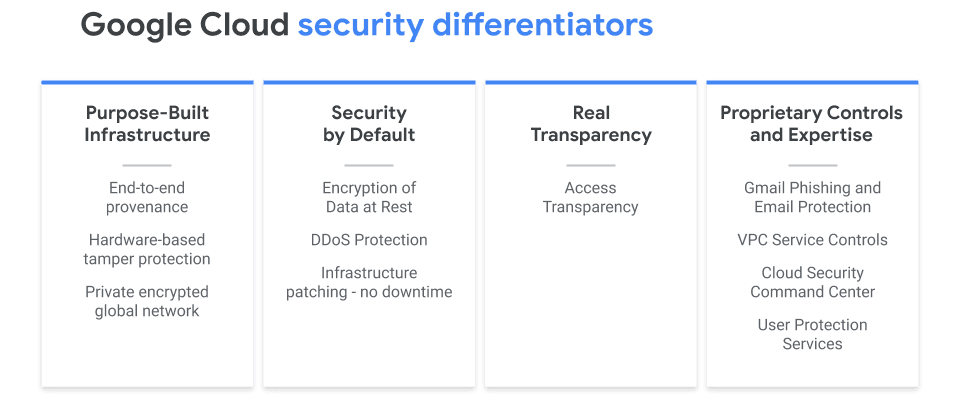 |
Click here for more information on Purpose Built Infrastructure and how Titan P protects from “man in the middle” attacks.
For more information on how Live Migration protects from any network down time, click here. |
The real transparency is truly key here. Google enables something they call Access Transparency, which allows the customer to monitor everything that the GCP service provider partner does within their environment. If a customer were to issue a ticket for support, they can see who at Google is accessing their environment and exactly what actions they are taking. Nothing is ever behind a curtain.
It goes without saying that cloud security requires collaboration. Anytime anyone talks about the public cloud – no matter the provider – there is a shared responsibility between the customer and that provider. GCP sets customers up for success by providing templates, best practices, and additional products to help customers do the additional work required to secure their own data before it reaches the public cloud.
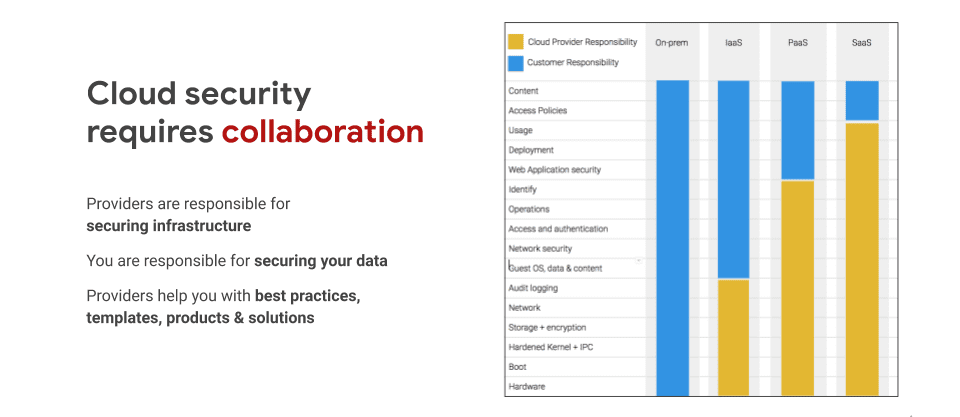
This is especially important when we’re talking about the scope of compliance. There’s a lot of secure foundational controls that GCP provides, but there are still international data compliances and regulations that must be followed by the customer. Customers must configure their environment in order to meet these international regulations.
GKE Deployment and the Benefits of Containerization
Now, let’s talk about container benefits. What exactly is a container? When we look at the history of tech development, we have what is called bare metal first, where customers were responsible for everything – OS, hardware, app code, dependencies – the whole stack. Then, the next iteration brought us VMs, where hardware maintenance was taken out of the equation, but companies still had to worry about everything else. Now, containers function as that next layer of abstraction – think about it as software on top of software – now, you don’t have to worry about OS maintenance or even virtual machines.
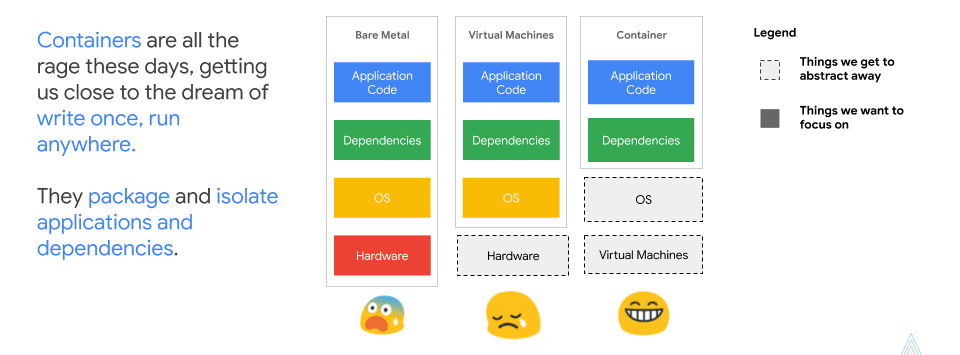
It’s a pretty interesting model to move into because it has unique security implications.
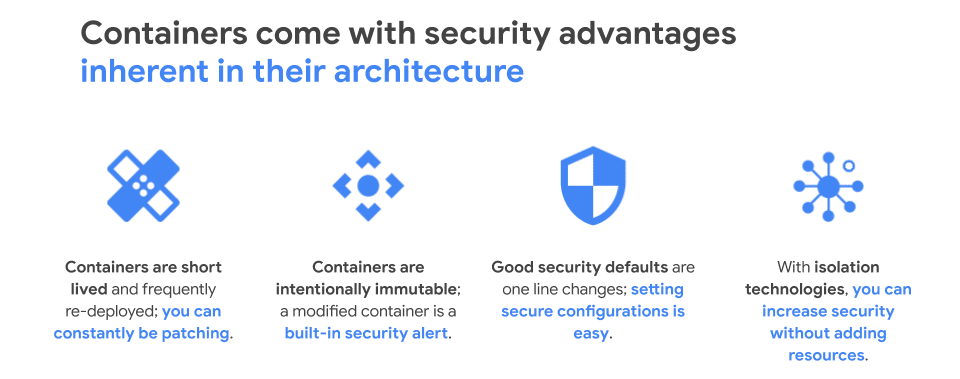
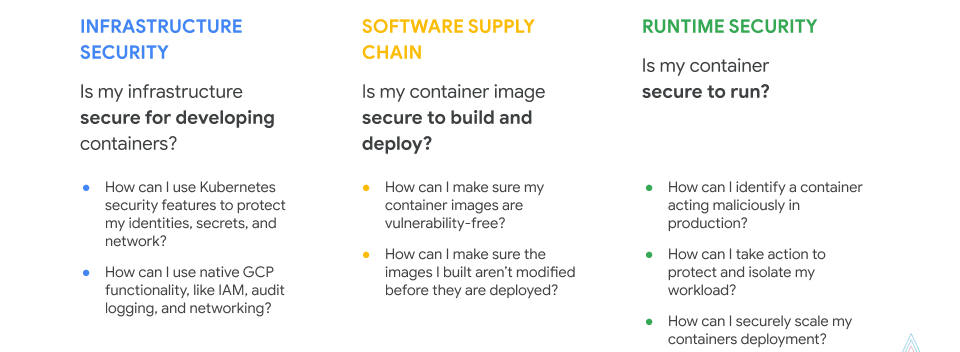
There are three definitive buckets to look at with container security:
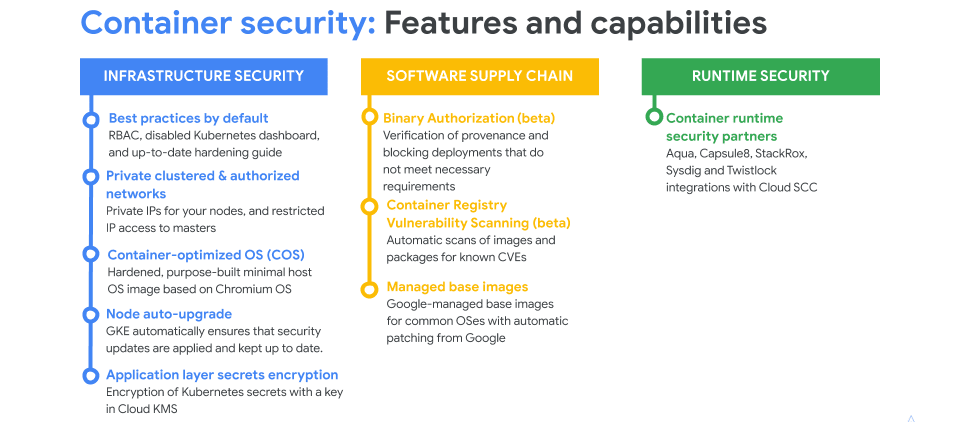
Google’s container security philosophy is three-fold. Google stands by the power of this container infrastructure because it allows for deep foundational security without the customer needing to be a security expert. They also employ integration with IAM, Audit Logging, VPCs, node auto-upgrades and are differentiated by the Cloud Security Command Center.
The Future of Cloud Security
Google believes in confidential VMs. That’s something they currently have in beta. It’s essentially highly-performant, inline encryption. It’s a checkbox that ensures that the hardware the virtual machine is running on has no insight into what the customer’s machine itself is doing. It scales beautifully so there is no refactoring of applications.
According to Lewis, the future also lies in shared workloads. This is for customers who have to deal with fed ramps. The idea is that Google can have restrictions on personnel, on data locations, etc., so that they can meet customers where they are so there’s no need for laborious customization.
There’s an exciting future ahead for the cloud, Kubernetes containerization and generally, for a world where customers feel increasingly secure with how and where their data is housed, accessed and controlled.
For more information on why we partner with GCP and chose them as our cloud partner, watch this webcast with Lucidworks’ own CEO, Will Hayes. Further reading on the business benefits of cloud computing.